Logging refers to the recording of event messages, e.g., regarding settings that have been made, the application of firewall rules, errors, etc.
Log entries are recorded in various categories and can be sorted and displayed according to these categories (see “Logging >> Browse Local Logs” on page 411).

All log entries are recorded in the RAM of the mGuard by default. Once the maximum memory space for log entries has been used up, the oldest log entries are automatically overwritten by new entries. In addition, all log entries are deleted when the mGuard is switched off.
To prevent this, log entries can be transmitted to an external computer (remote server). This is particularly useful if you wish to manage the logs of multiple mGuard devices centrally.
|
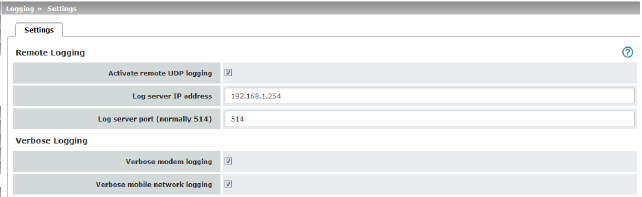
Remote Logging |
Activate remote UDP logging |
If you want all log entries to be transmitted to the external log server (specified below), activate the function. |
|
|
Log server IP address |
Specify the IP address of the log server to which the log entries should be transmitted via UDP. An IP address must be specified, not a host name. This function does not support name resolution because it might not be possible to make log entries if a DNS server fails. |
|
|
Log server port |
Specify the port of the log server to which the log entries should be transmitted via UDP. Default: 514 |
|
|

|
|
|
|
–If the IPsec VPN >> Connections >> Edit >> General, Local option is set to 1:1 NAT (see page 336), the following applies: The internal IP address must be located in the specified local network. –If the IPsec VPN >> Connections >> Edit >> General, Remote option is set to 1:1 NAT (see page 338), the following applies: The IP address of the remote log server must be located in the network that is specified as Remote in the definition of the VPN connection. |
|
|
Verbose logging |
Verbose modem logging |
Only available if an internal or external modem is available and switched on. –Internal modem: TC MGUARD RS4000/RS2000 3G, TC MGUARD RS4000/RS2000 4G, FL MGUARD RS with internal analog modem or ISDN modem –External modem: FL MGUARD RS4000/RS2000, TC MGUARD RS4000/RS2000 3G, TC MGUARD RS4000/RS2000 4G, FL MGUARD RS4004/RS2005, mGuard Centerport (Innominate), FL MGUARD CENTERPORT, FL MGUARD RS, FL MGUARD BLADE, mGuard delta (Innominate), FL MGUARD DELTA Verbose logging |
|
|
Verbose mobile network logging |
Only available with the TC MGUARD RS4000/RS2000 3G, TC MGUARD RS4000/RS2000 4G Verbose logging |
15.2Logging >> Browse Local Logs
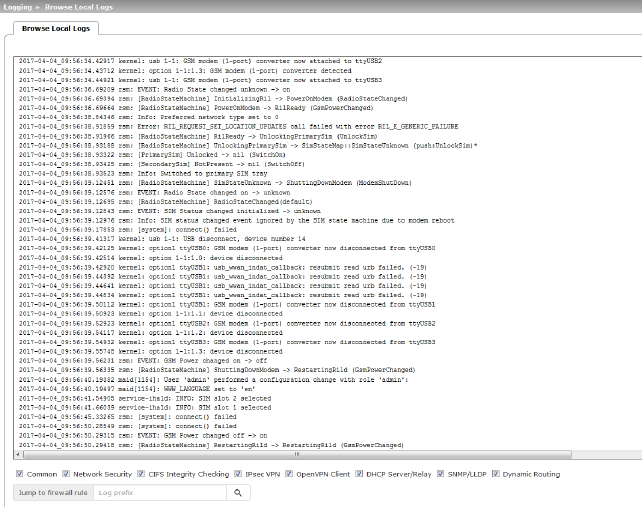
The corresponding check boxes for filtering entries according to their category are displayed below the log entries, depending on which mGuard functions were active.
To display one or more categories, enable the check boxes for the desired categories. The log entries are continuously updated according to the selection.
To pause or continue the continuous updating of the log entries, click on the  Pause or
Pause or  Continue button.
Continue button.
Access to log entries
The log entries can be accessed in various ways
|
mGuard |
UDP |
Web interface (web UI) |
|---|---|---|
|
/var/log/cifsscand |
socklog |
CIFS Integrity Checking |
|
/var/log/dhclient |
No |
Common |
|
/var/log/dhcp-ext |
No |
DHCP Server/Relay |
|
/var/log/dhcp-int |
No |
DHCP Server/Relay |
|
/var/log/dnscache |
No |
No |
|
/var/log/dynrouting |
socklog |
Dynamic Routing |
|
/var/log/firestarter |
svlogd |
IPsec VPN |
|
/var/log/firewall |
svlogd |
Network Security |
|
/var/log/fwrulesetd |
socklog |
Network Security |
|
/var/log/gsm |
No |
Common |
|
/var/log/https |
No |
No |
|
/var/log/ipsec |
socklog |
IPsec VPN |
|
/var/log/l2tp |
No |
IPsec VPN |
|
/var/log/lldpd |
No |
SNMP/LLDP |
|
/var/log/login |
No |
No |
|
/var/log/maid |
No |
No |
|
/var/log/main |
socklog |
Common |
|
/var/log/maitrigger |
No |
No |
|
/var/log/openvpn |
socklog |
OpenVPN Client |
|
/var/log/pluto |
svlogd |
IPsec VPN |
|
/var/log/psm-sanitize |
No |
Common |
|
/var/log/pullconfig |
socklog |
Common |
|
/var/log/redundancy |
socklog |
Common |
|
/var/log/snmp |
No |
SNMP/LLDP |
|
/var/log/tinydns |
No |
Common |
|
/var/log/userfwd |
socklog |
Network Security |
.
|
Logging >> Browse Local Logs >> Categories |
|
|---|---|
|
General |
Log entries that cannot be assigned to other categories. |
|
Network Security |
Logged events are shown here if the logging of events was selected when defining the firewall rules (Log = enabled). Log ID and number for tracing errors Log entries that relate to the firewall rules listed below have a log ID and number. This log ID and number can be used to trace the firewall rule to which the corresponding log entry relates and that led to the corresponding event. Firewall rules and their log ID –Packet filters: Network Security >> Packet Filter >> Incoming Rules menu Network Security >> Packet Filter >> Outgoing Rules menu Log ID: fw-incoming or fw-outgoing –Firewall rules for VPN connections: IPsec VPN >> Connections >> Edit >> Firewall menu, Incoming/Outgoing Log ID: fw-vpn-in or fw-vpn-out |
|
|
–Firewall rules for OpenVPN connections: OpenVPN Client >> Connections >> Edit >> Firewall menu, Incoming/Outgoing Log ID: fw-openvpn-in or fw-openvpn-out OpenVPN Client >> Connections >> Edit >> NAT menu Log ID: fw-openvpn-portfw –Firewall rules for web access to the mGuard via HTTPS: Management >> Web Settings >> Access menu Log ID: fw-https-access |
|
|
–Firewall rules for access to the mGuard via SNMP: Management >> SNMP >> Query menu Log ID: fw-snmp-access –Firewall rules for SSH remote access to the mGuard: Management >> System Settings >> Shell Access menu Log ID: fw-ssh-access –Firewall rules for access to the mGuard via NTP: Management >> System Settings >> Time and Date menu Log ID: fw-ntp-access |
|
|
–Firewall rules for the user firewall: Network Security >> User Firewall menu, Firewall Rules Log ID: ufw- –Rules for NAT, port forwarding: Network >> NAT >> IP and Port Forwarding menu Log ID: fw-portforwarding |
|
|
–Firewall rules for the serial interface: Network >> Interfaces >> Dial-in menu Incoming rules: log ID: fw-serial-incoming Outgoing rules: log ID: fw-serial-outgoing
Searching for firewall rules based on a network security log As of mGuard firmware version 8.6.0, firewall log entries in the list are highlighted in blue and provided with a hyperlink. A click on the firewall log entry, e. g. fw-https-access-1-1ec2c133-dca1-1231-bfa5-000cbe01010a opens the configuration page (menu >> submenu >> tab) with the firewall rule that caused the log entry. When using mGuard firmware versions < 8.6.0, proceed as follows: If the Network Security check box is enabled so that the relevant log entries are displayed, the Jump to firewall rule search field is displayed below the Reload logs button. Proceed as follows if you want to trace the firewall rule referenced by a log entry in the Network Security category and which resulted in the corresponding event: Proceed as follows if you want to trace the firewall rule referenced by a log entry in the Network Security category and which resulted in the corresponding event: 1.Select the section that contains the log ID and number in the relevant log entry, for example: fw-https-access-1-1ec2c133-dca1-1231-bfa5-000cbe01010a 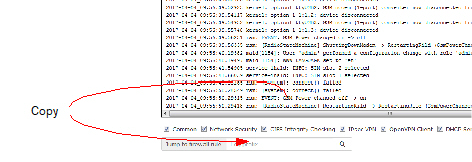
2.Copy this section to the Jump to firewall rule field. 3.Click on the Lookup button. The configuration page containing the firewall rule that the log entry refers to is displayed. |
|
FL MGUARD BLADE |
In addition to error messages, the following messages are output on the FL MGUARD BLADE controller: (The areas enclosed by < and > are replaced by the relevant data in the log entries.) General messages: blade daemon "<version>" starting ... Blade[<bladenr>] online Blade[<bladenr>] is mute Blade[<bladenr>] not running Reading timestamp from blade[<bladenr>] When activating a configuration profile on a blade: Push configuration to blade[<bladenr>] reconfiguration of blade[<bladenr>] returned <returncode> blade[<bladenr>] # <text> When retrieving a configuration profile from a blade: Pull configuration from blade[<bladenr>] Pull configuration from blade[<bladenr>] returned <returncode> |
|
CIFS Integrity Checking |
Messages relating to the integrity check of network drives are displayed in this log. In addition, messages that occur when connecting the network drives and are required for the integrity check are also visible. |
|
IPsec VPN |
Lists all VPN events. The format corresponds to standard Linux format. There are special evaluation programs that present information from the logged data in a more easily readable format. |
|
OpenVPN Client |
Lists all OpenVPN events. |
|
DHCP Server/Relay |
Messages from the services that can be configured under Network >> DHCP.
|
|
SNMP/LLDP |
Messages from the services that can be configured under Management >> SNMP. |
|
Dynamic Routing |
Lists all events that are generated by dynamic routing. |