The mGuard supports the use of an SEC-Stick, which is an access protector for IT systems. The SEC-Stick is a product from team2work: www.team2work.de.
The SEC-Stick is essentially a key. The user inserts it into the USB port of a computer with an Internet connection, and can then set up an encrypted connection to the mGuard in order to securely access defined services in the office or home network. The Remote Desktop Protocol, for example, can be used within the encrypted and secure SEC-Stick connection to control a PC remotely in the office or at home, as if the user was sitting directly in front of it.
In order for this to work, access to the business PC is protected by the mGuard and the mGuard must be configured for the SEC-Stick to permit access. This is because the user of this remote computer, into which the SEC-Stick is inserted, authenticates himself/herself to the mGuard using the data and software stored on his/her SEC-Stick.
The SEC-Stick establishes an SSH connection to the mGuard. Additional tunnels can be embedded into this connection, e.g., TCP/IP connections.

|
SEC-Stick >> Global >> Access |
||
|---|---|---|
|
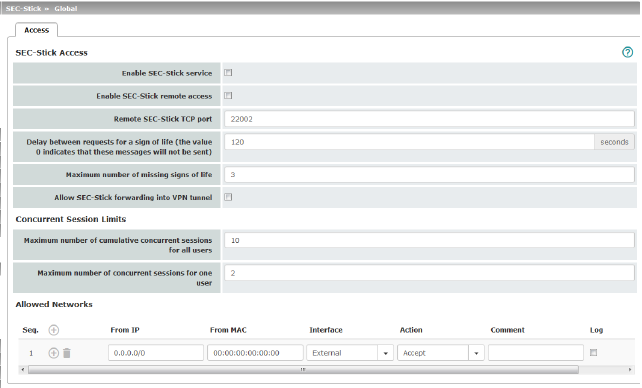
SEC-Stick Access (This menu item is not included in the scope of functions for TC MGUARD RS2000 3G, TC MGUARD RS2000 4G, FL MGUARD RS2005 or FL MGUARD RS2000.) |

|
|
|
|
Enable SEC-Stick service |
When activated, the function specifies that the SEC-Stick being used at a remote location or its owner can log in. In this case, SEC-Stick remote access must also be enabled (next option). |
|
|
When the function is activated, SEC-Stick remote access is enabled. |
|
|
|
Remote SEC-Stick TCP port |
Default: 22002 If this port number is changed, the new port number only applies for access via the External, External 2, DMZ, GRE or VPN interface. Port number 22002 still applies for internal access. |
|
|
Default: 120 seconds Values from 0 to 3600 seconds can be set. Positive values indicate that the mGuard is sending a request to the peer within the encrypted SSH connection to find out whether it can still be accessed. This request is sent if no activity was detected from the peer for the specified number of seconds (e.g., due to network traffic within the encrypted connection). The value entered here relates to the functionality of the encrypted SSH connection. As long as it is working properly, the SSH connection is not terminated by the mGuard as a result of this setting, even when the user does not perform any actions during this time. As the number of simultaneously open sessions is limited (see Maximum number of cumulative concurrent sessions for all users), it is important to terminate sessions that have expired. Therefore, the request for a sign of life is preset to 120 seconds for Version 7.4.0 or later. If a maximum of three requests for a sign of life are issued, this causes an expired session to be detected and removed after six minutes. In previous versions, the preset was “0”. This means that no requests for a sign of life are sent. Please note that sign of life requests generate additional traffic. |
|
|
|
Maximum number of missing signs of life |
Specifies the maximum number of times a sign of life request to the peer may remain unanswered. For example, if a sign of life request should be made every 15 seconds and this value is set to 3, the SEC-Stick client connection is deleted if a sign of life is not detected after approximately 45 seconds. |
|
|
Allow SEC-Stick forwarding into VPN tunnel |
Allows SSH connections to be forwarded in a VPN tunnel (Hub & Spoke). |
|
Concurrent Session Limits |
The number of simultaneous sessions is limited for SEC-Stick connections. Approximately 0.5 MB of memory are required for each session to ensure the maximum level of security. The restriction does not affect existing sessions; it only affects newly established connections. |
|
|
|
Maximum number of cumulative concurrent sessions for all users |
0 to 2147483647 Specifies the number of connections that are permitted for all users simultaneously. When “0” is set, no session is permitted. |
|
|
Maximum number of concurrent sessions for one user |
0 to 2147483647 Specifies the number of connections that are permitted for one user simultaneously. When “0” is set, no session is permitted. |
|
Allowed Networks |
Lists the firewall rules that have been set up for SEC-Stick remote access |
|
|
|
If multiple firewall rules are defined, these are queried starting from the top of the list of entries until an appropriate rule is found. This rule is then applied. If the list of rules contains further subsequent rules that could also apply, these rules are ignored. Multiple rules can be specified. |
|
|
|
Enter the address of the computer/network from which access is permitted or forbidden in this field. IP address: 0.0.0.0/0 means all addresses. To specify an address area, use CIDR format (see “CIDR (Classless Inter-Domain Routing)” on page 29). |
|
|
|
Interface |
Internal / External / External 2 / DMZ / VPN / GRE / Dial-in1 Specifies to which interface the rule should apply. If no rules are set or if no rule applies, the following default settings apply: –SEC-Stick remote access is permitted via Internal, DMZ, VPN, and Dial-in. –Access via External, External 2, and GRE is denied. Specify the access options according to your requirements. 
|
|
|
Action |
Accept means that the data packets may pass through. Reject means that the data packets are sent back and the sender is informed of their rejection. (In Stealth mode, Reject has the same effect as Drop.) Drop means that the data packets are not permitted to pass through. They are discarded, which means that the sender is not informed of their whereabouts. Name of rule sets, if defined. When a name is specified for rule sets, the firewall rules saved under this name take effect (see Rule Records tab page). 
|
|
|
Comment |
Freely selectable comment for this rule. |
|
|
Log |
For each individual firewall rule, you can specify whether the use of the rule: –Should be logged – set Log to Yes –Should not be logged – set Log to No (default setting) |
|
1External 2 and Dial-in are only for devices with a serial interface (see “Network >> Interfaces” on page 131). |
|
SEC-Stick >> Connections >> SEC-Stick Connections |
||
|---|---|---|
|
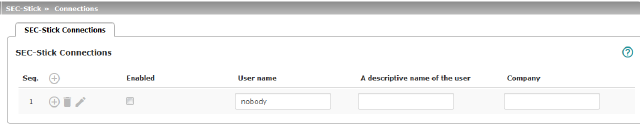
List of defined SEC-Stick connections. 
|
||
|
|
Enabled |
To use a defined SEC-Stick connection, the Enabled option must be activated. |
|
|
User name |
An SEC-Stick connection with a uniquely assigned user name must be defined for every owner of an SEC-Stick who has authorized access. This user name is used to uniquely identify the defined connections. |
|
|
Name of the person. |
|
|
|
Company |
Name of the company. |
|
|
The following page appears when you click on the |
|
|
||
|
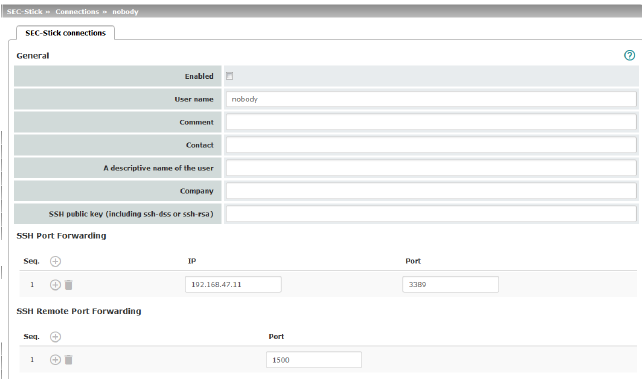
General |
Enabled |
As above |
|
|
User name |
As above |
|
|
Comment |
Optional comment text. |
|
|
Optional comment text. |
|
|
|
A descriptive name of the user |
Optional: name of the person (repeated) |
|
|
Company |
Optional: as above |
|
|
SSH public key (including ssh-dss or ssh-rsa) |
Enter the SSH public key belonging to the SEC-Stick in ASCII format in this field. The secret equivalent is stored on the SEC-Stick. |
|
SSH Port Forwarding |
List of allowed access and SSH port forwarding relating to the SEC-Stick of the corresponding user. |
|
|
|
IP address of the computer to which access is enabled. |
|
|
|
Port |
Port number to be used when accessing the computer. |
|
SSH Remote Port Forwarding |
Port |
Port that is used for SSH remote port forwarding. |