
For additional information on the device as well as release notes and software updates, visit: phoenixcontact.net/products.
The mGuard protects IP data links by combining the following functions:
–Industrial security network router (with built-in 4 or 5-port switch and DMZ port depending on the model).
–VPN router for secure data transmission via public networks (hardware-based DES, 3DES, and AES encryption, IPsec and OpenVPN protocol).
–Configurable firewall for protection against unauthorized access. The dynamic packet filter inspects data packets using the source and destination address and blocks undesired data traffic.
1.1Basic properties of the mGuards
The mentioned properties are not guaranteed properties, as they are basically dependent on the respective device and on installed licenses.
Network features
–Stealth (auto, static, multi), router (static, DHCP client), PPPoE (for DSL), PPTP (for DSL), and modem
–VLAN
–DHCP server/relay on the internal and external network interfaces
–DNS cache on the internal network interface
–Dynamic routing (OSPF)
–GRE tunneling
–Administration via HTTPS and SSH
–Optional conversion of DSCP/TOS values (Quality of Service)
–Quality of Service (QoS)
–LLDP
–MAU management
–SNMP
Firewall features
–Stateful packet inspection
–Anti-spoofing
–IP filter
–L2 filter (only in stealth mode)
–NAT with FTP, IRC, and PPTP support (only in “Router” network mode)
–1:1 NAT (only in “Router” network mode)
–Port forwarding (not in “Stealth” network mode)
–Individual firewall rules for different users (user firewall)
–Individual rule sets as action (target) of firewall rules (apart from user firewall or VPN firewall)
Anti-virus features
–CIFS integrity check of network drives for changes to specific file types (e.g., executable files)
VPN features (IPsec)
–Protocol: IPsec (tunnel and transport mode, XAuth/Mode Config)
–IPsec encryption in hardware with DES (56 bits), 3DES (168 bits), and AES (128, 192, 256 bits)
–Packet authentication: MD5, SHA-1, SHA-265, SHA-384, SHA-512
–Internet Key Exchange (IKE) with main and quick mode
–Authentication via:
–Pre-shared key (PSK)
–X.509v3 certificates with public key infrastructure (PKI) with certification authority (CA), optional certificate revocation list (CRL), and the option of filtering by subject
or
–Remote certificate, e.g., self-signed certificates
–Detection of changing peer IP addresses via DynDNS
–NAT traversal (NAT-T)
–Dead Peer Detection (DPD): detection of IPsec connection aborts
–IPsec/L2TP server: connection of IPsec/L2TP clients
–IPsec firewall and 1:1 NAT
–Default route via VPN tunnel
–Data forwarding between VPNs (hub and spoke)
–Depending on the license: up to 250 VPN tunnels, in the case of mGuard Centerport (Innominate)/FL MGUARD CENTERPORT up to 3000 active VPN tunnels
–Hardware acceleration for encryption in the VPN tunnel (except for mGuard Centerport (Innominate)/FL MGUARD CENTERPORT)
VPN features (OpenVPN)
–OpenVPN client
–OpenVPN encryption with Blowfish, AES (128, 192, 256 bits)
–Dead Peer Detection (DPD)
–Authentication via user identifier, password or X.509v3 certificate
–Detection of changing peer IP addresses via DynDNS
–OpenVPN firewall and 1:1 NAT
–Routes via VPN tunnels can be configured statically and learned dynamically
–Data forwarding between VPNs (hub and spoke)
–Depending on the license: up to 50 VPN tunnels
Additional features
–Remote Logging
–VPN/firewall redundancy (depending on the license)
–Administration using SNMP v1 - v3 and Phoenix Contact Device Manager (mGuard device manager (FL MGUARD DM))
–PKI support for HTTPS/SSH remote access
–Can act as an NTP and DNS server via the LAN interface
–Compatible with mGuard Secure Cloud
–Plug-n-Protect technology
–Tracking and time synchronization via GPS/GLONASS positioning system (product-dependent)
–COM Server
Support
In the event of problems with your mGuard, please contact your supplier.
|
For additional information on the device as well as release notes and software updates, visit: phoenixcontact.net/products. |
1.2Typical application scenarios
This section describes various application scenarios for the mGuard.
–Stealth mode (Plug-n-Protect)
–DMZ (demilitarized zone)
–WLAN via VPN tunnel
–Mobile router via integrated mobile network modem
1.2.1Stealth mode (Plug-n-Protect)
In stealth mode, the mGuard can be positioned between an individual computer and the rest of the network.
The settings (e.g., for firewall and VPN) can be made using a web browser under the URL https://1.1.1.1/.
No configuration modifications are required on the computer itself.
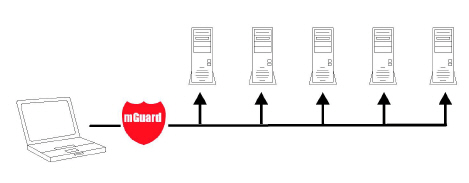
Figure 1-1: Stealth mode (Plug-n-Protect)
When used as a network router, the mGuard can provide the Internet connection for several computers and protect the company network with its firewall.
One of the following network modes can be used on the mGuard:
–Router, if the Internet connection is, for example, via a DSL router or a permanent line.
–PPPoE, if the Internet connection is, for example, via a DSL modem and the PPPoE protocol is used (e.g., in Germany).
–PPTP, if the Internet connection is, for example, via a DSL modem and the PPTP protocol is used (e.g., in Austria).
–Modem, if the Internet connection is via a serial connected modem (compatible with Hayes or AT command set).
–Built-in mobile network modem, mobile router via integrated mobile network modem
For computers in the Intranet, the mGuard must be specified as the default gateway.

Figure 1-2: Network router
A DMZ (demilitarized zone) is a protected network that is located between two other networks. For example, a company's website may be in the DMZ so that new pages can only be copied to the server from the Intranet via FTP. However, the pages can be read from the Internet via HTTP.
IP addresses within the DMZ can be public or private, and the mGuard, which is connected to the Internet, forwards the connections to private addresses within the DMZ by means of port forwarding.
A DMZ scenario can be established either between two mGuards (see Figure 1-3) or via a dedicated DMZ port of the TC MGUARD RS4000 3G, TC MGUARD RS4000 4G or FL MGUARD RS4004.
The DMZ port is only supported in router mode and requires at least one IP address and a corresponding subnet mask. The DMZ does not support any VLANs.

The VPN gateway provides company employees with encrypted access to the company network from home or when traveling. The mGuard performs the role of the VPN gateway.
IPsec-capable VPN client software must be installed on the external computers or failing that, the computer is equipped with an mGuard.
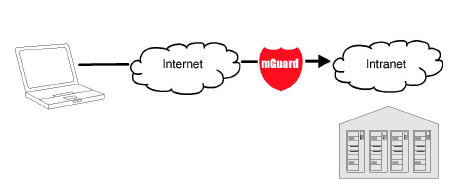
Figure 1-4: VPN gateway
WLAN via VPN is used to connect two company buildings via a WLAN path protected using IPsec. The adjacent building should also be able to use the Internet connection of the main building.

Figure 1-5: WLAN via VPN
In this example, the mGuards were set to router mode and a separate network with 172.16.1.x addresses was set up for the WLAN.
To provide the adjacent building with an Internet connection via the VPN, a default route is set up via the VPN:
Tunnel configuration in the adjacent building
|
Connection type |
Tunnel (network <-> network) |
|
Address of the local network |
192.168.2.0/24 |
|
Address of the remote network |
0.0.0.0/0 |
In the main building, the corresponding counterpart is configured:
Tunnel configuration in the main building
|
Connection type |
Tunnel (network <-> network) |
|
Local network |
0.0.0.0 |
|
Address of the remote network |
192.168.2.0/24 |
The default route of an mGuard usually uses the WAN port. However, in this case the Internet can be accessed via the LAN port:
Default gateway in the main building:
|
IP address of the default gateway |
192.168.1.253 |
1.2.6Resolving network conflicts
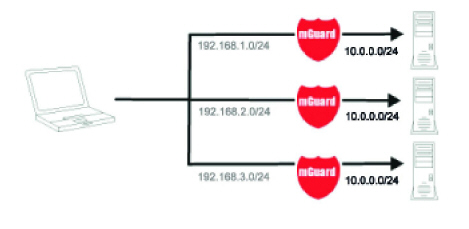
Resolving network conflicts
In the example, the networks on the right-hand side should be accessible to the network or computer on the left-hand side. However, for historical or technical reasons the networks on the right-hand side overlap.
The 1:1 NAT feature of the mGuard can be used to translate these networks to other networks, thereby resolving the conflict.
(1:1 NAT can be used in normal routing and in IPsec tunnels and in OpenVPN connections.)