12Support menu
|
Support >> Advanced >> Tools |
||
|---|---|---|
|
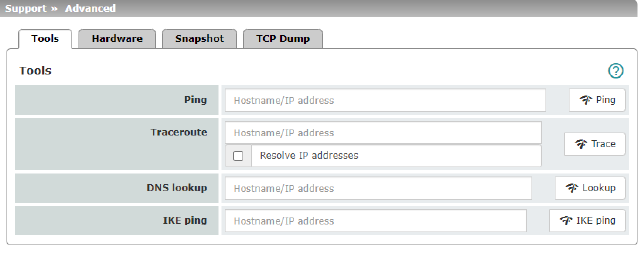
Ping |
Aim: to check whether a peer can be reached via a network. Procedure: •Enter the IP address or host name of the peer in the Hostname/IP Address field. Then click on the Ping button. A corresponding message is then displayed. |
|
|
Traceroute |
Aim: to determine which intermediate points or routers are located on the connection path to a peer. Procedure: •Enter the host name or IP address of the peer whose route is to be determined in the Hostname/IP Address field. •If the points on the route are to be output with IP addresses instead of host names (if applicable), activate the Do not resolve IP addresses to hostnames check box (check mark). •Then click on the Trace button. A corresponding message is then displayed. |
|
|
DNS lookup |
Aim: to determine which host name belongs to a specific IP address or which IP address belongs to a specific host name. Procedure: •Enter the IP address or host name in the Hostname field. •Click on the Lookup button. The response, which is determined by the mGuard according to the DNS configuration, is then returned. |
|
|
IKE ping |
Aim: to determine whether the VPN software for a VPN gateway is able to establish a VPN connection, or whether a firewall prevents this, for example. Procedure: •Enter the name or IP address of the VPN gateway in the Hostname/IP Address field. •Click on the IKE ping button. •A corresponding message is then displayed. |
|

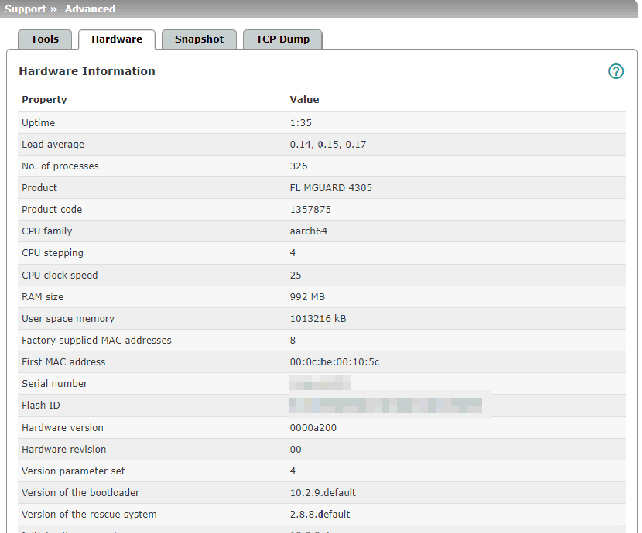
This page lists various hardware properties of the mGuard.
MAC addresses
The MAC address of the WAN interface determined by the manufacturer is indicated on the type label of the device. The other MAC addresses (LAN/DMZ [optional]) can be calculated as follows:
–WAN interface: see type label.
–LAN interface: MAC address of the WAN interface incremented by 1 (WAN + 1).
Devices with integrated switch: all switch ports use the same MAC address.
–DMZ interface: MAC address of the WAN interface incremented by 4 (WAN + 4).
Example:
–WAN: 00:a0:45:eb:28:9d
–LAN: 00:a0:45:eb:28:9e
–DMZ: 00:a0:45:eb:28:a1
|
Support >> Advanced >> Snapshot |
||
|---|---|---|
|
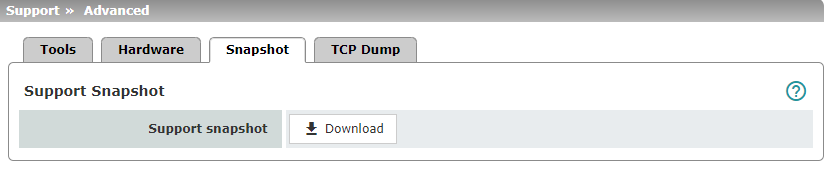
Support Snapshot |
Support snapshot |
Creates a compressed file (in tar.gz format) containing all current configuration settings that could be relevant for error diagnostics. 
To create a Support snapshot or Support snapshot with persistent logs, proceed as follows: •Click on the Download button. •Save the file (under the name snapshot-YYYY.MM.DD-hh.mm.ss.tar.gz or snapshot-all-YYYY.MM.DD-hh.mm.ss.tar.gz). Provide the file to the support team of your supplier, if required. |
|
Support >> Advanced >> Snapshot |
||
|---|---|---|
|
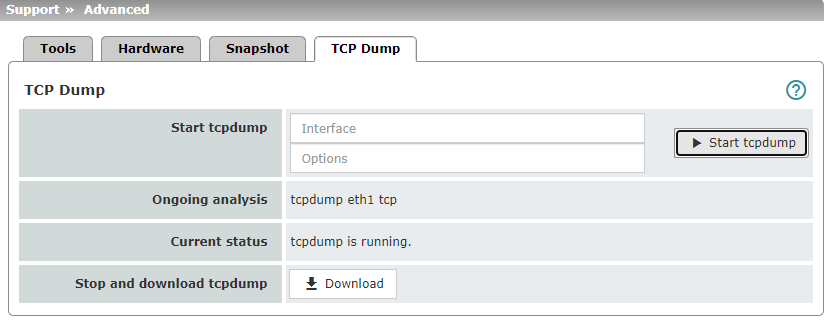
TCP Dump |
A packet analysis (tcpdump) can be used to analyze the content of network packets that are sent or received via a selected network interface. Filter options are used to determine which network packets are analyzed. The result of the analysis is saved in a file (*.tar.gz), downloaded and deleted on the device. 
|
|
|
|
Start tcpdump
|
Interface Only data packets that are sent or received via the selected network interface will be analyzed. –WAN interface (XF1): –eth0 –LAN interface (XF2-4 or 2-5): –eth1 (network mode Router only) –br0 (network mode Stealth only) –swp0 (FL MGUARD 2105/4305 only) –swp1 (FL MGUARD 2105/4305 only) –swp2 (FL MGUARD 2105/4305 only) –swp3 (FL MGUARD 2105 only) –DMZ interface (XF5): –dmz0 (FL MGUARD 4305 only)
|
|
|
|
Options By specifying options, the packet analysis can be restricted to a selection of the elements listed below. Options can be linked via the logical operators "and, or, not". Example: tcp and net 192.168.1.0/24 and not port 443 |
|
|
|
Available options: –tcp: TCP protocol –udp: UDP protocol –arp: ARP protocol –icmp: ICMP protocol –esp: ESP protocol –host <ip>: IPv4 address –port <1-65535>:Network port (port number or service name) –net <nw_cidr>: Network (in CIDR format, e.g. 192.168.1.0/24) –and, or, not: Logical operators "start tcpdump" button •Click on the "Start tcpdump" button to start an analysis. |
|
|
Ongoing analysis |
During a running analysis: shows for which interface and with which options tcpdump is being executed. |
|
|
Current status |
Shows the status of the analysis. |
|
|
Stop and download tcpdump |
"Download" button •Click on the Download button, –to stop a running analysis and download the data or –to download data that has been saved on the device after an automatically stopped analysis. The recorded package contents are summarized in a file (*.tar.gz) and automatically downloaded from the device. The file is then deleted from the device. The time at which the file was downloaded is specified in the file name as follows: <YYYY.MM.DD-hh.mm.ss> Example: tcpdump-2024.06.10-09.47.54.tar.gz
|